Tools needed: InVid-WeVerify plugin installed in Chrome or Firefox
Skill Level: Intermediate – some verification knowledge required
One of the main tools we at Amnesty International’s Evidence Lab recommend to all open source investigators is the InVid-WeVerify web browser plugin for Chrome or Firefox. It is built as a Swiss Army Knife for verification, containing several tools in one place, including a keyframe extractor for videos, a metadata extractor for photos and videos, a reverse image search on keyframes, a magnifying tool for photographs, and a neat interface for Twitter Advanced Search. We explain how many of these features work in this blog post, which is adapted from much of the tutorials available in the plug-in.
This tool is the result of the InVid (or In Video Veritas) and WeVerify collaborations funded by the European Union. The goal is to help journalists, human rights investigators and other researchers verify content on social networks.
When the tool is installed, a small launcher icon appears at the top of the browser.

LAUNCHING INVID-WEVERIFY
When clicked, the launcher gives the user three options.
Open InVID launches the plugin.
Video Urls displays the url of a video present on a web page.
Image Urls displays the url of an image present on a web page.

The latter two options can be particularly useful if a photo or video is embedded in a news site, for instance. Copy and paste the urls to use them when InVid-WeVerify is opened.
OPENING INVID-WEVERIFY
Once the tool is opened, the user will see several tabs.

We address each of these tabs below (except the Video Rights tab, which is aimed at journalists dealing with copyright issues).
The Analysis tab is an enhanced metadata viewer for YouTube, Twitter and Facebook public videos. It allows the user to retrieve contextual information, location (if detected), most interesting comments, and apply a reverse image search and check for tweets on the video (on YouTube). For Facebook, the user needs to be logged in to a Facebook account to be able to process links.
The Keyframes tab allows the user to copy a video url (from YouTube, Twitter, Facebook, Daily Motion or Dropbox) or to upload a local video file (in mp4, webm, avi, mov, wmv, ogv, mpg, flv, and mkv format) in order to segment the video into keyframes. Once segmented, the keyframes can be searched with a left click on Google Image Search or with the contextual menu (right click) on Google, Yandex, Tineye, Bing, Karma Decay (for Reddit) and Baidu images.
The YouTube Thumbnails tab allows the user to quickly trigger a reverse image search on Google, Bing, Tineye or Yandex Images with four thumbnails extracted from a YouTube video. Up to four tabs (according to the number of thumbnails available) are opened automatically in the browser with the results of the reverse image search, while the four thumbnails are also displayed in the plugin page. This tab is somewhat redundant with what can be done with the Analysis tab but it is very fast and efficient if a user needs to find out whether a YouTube video has been published before.
The Twitter search tab is an enhanced Twitter advanced search for keywords or hashtags using the since and until operators to narrow down the time interval of a query to within a minute. It automatically translates the calendar date, hour, and minute into a unix timestamp to facilitate the query, e.g., of the first pictures or videos within a time range just after a breaking news event. The tab also includes other features from Twitter advanced search, such as geocode, near, from, language and various filter operators.
The Magnifier tab allows a user to display an image through its url and to zoom or apply a magnifying lens on the image to help decode and read hard to see details in an image – such as car registration plates, military insignia, signs and banners. The user can either enter the image url or upload an image from a local drive with the local file button. Once the image is displayed from a url, you can Google, Yandex, Tineye and Baidu reverse image search on it or use the Image forensic tab explained below. Other tools available in this tab are sharpen, image flip, and crop.
The Metadata tab allows the user to check the Exif data of a jpeg picture, or the metadata of a video in mp4/m4v format. This is either through a link or a local file.
The Forensic tab provides eight different filters that can be applied to images to help the user to detect digital image tampering – such as the use of Photoshop editing software. This requires advanced knowledge of how image filters work, so the tab is not recommended for use by beginners to open source investigation.
THE CONTEXTUAL MENU
The InVid-WeVerify plug-in also brings a contextual menu to your browser. This is activated by a right-click on an image or a video url when online.
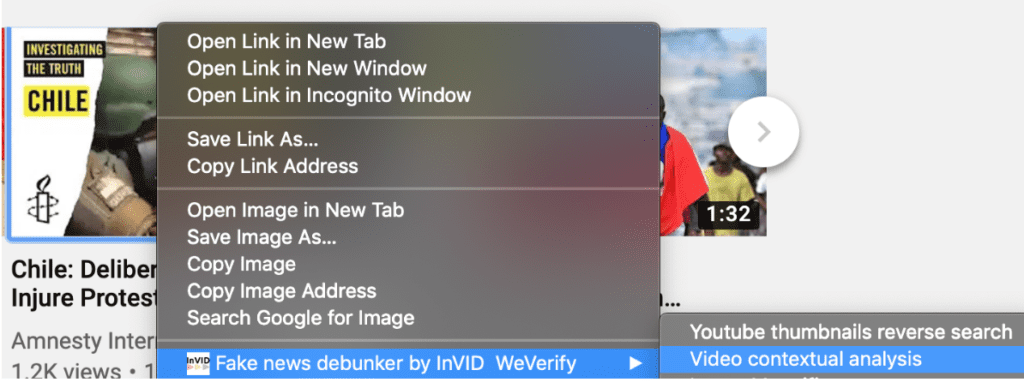
This menu allows the user to trigger this plug-in on a still image or on a YouTube video link. On an image, a right-click will propose either to open the picture in the Image magnifier to examine it more closely, or to launch forensic analysis or reverse image searches of this image. On a video link, a right-click will propose either an InVID-WeVerify video analysis or the YouTube thumbnail reverse search.
The InVid-WeVerify consortium is funded by the European Union Horizon 20:20 programme, and is composed of: Agence France-Presse, Deutsche Welle, Centre for Research and Technology Hellas (CERTH) – Information Technologies Institute (ITI), Modul Technology GmbH, Universitat de Lleida, Exo Makina, WebLyzard Technology GmbH, Condat AG, APA-IT Informations Technologie GmbH, The University of Sheffield, Athens Technology Center, and EU Disinfolab.
This article was partly adapted from the InVid-WeVerify Browser Plug-in tutorial authored by Denis Teyssou of Agence France-Presse.


